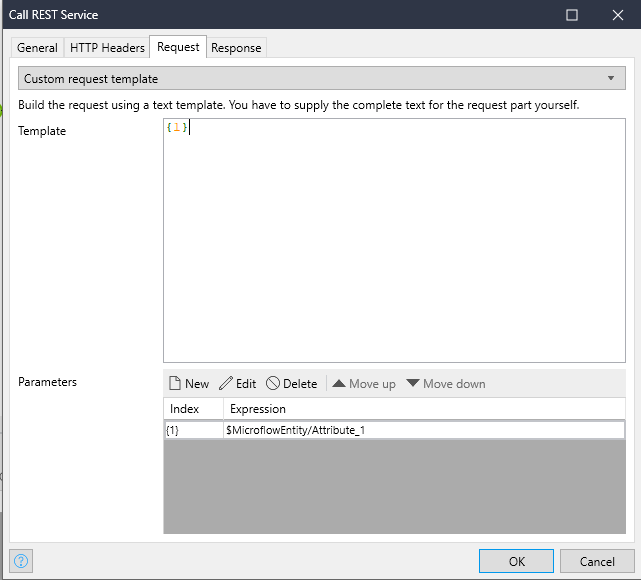
A string template as body for a REST call (or a web service call for that matter) can be used for an injection attack if the template has parameters that are not properly escaped. If somebody can influence the value of the parameter the resulting JSON can be manipulated.
This rule detects the places where a string template is used in a REST or web service call and the string template has parameters. This rule will not detect if the parameters are properly escaped or can be changed by the user. To solve this violation you can refactor to use an export mapping or escape the parameters and annotate to prevent the violation.
Non-compliant example:
Compliant example:
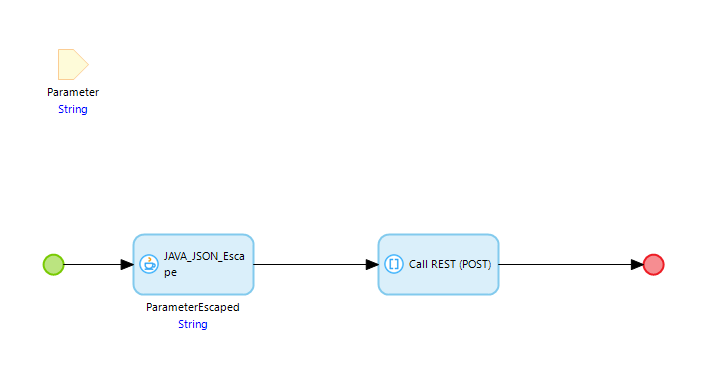
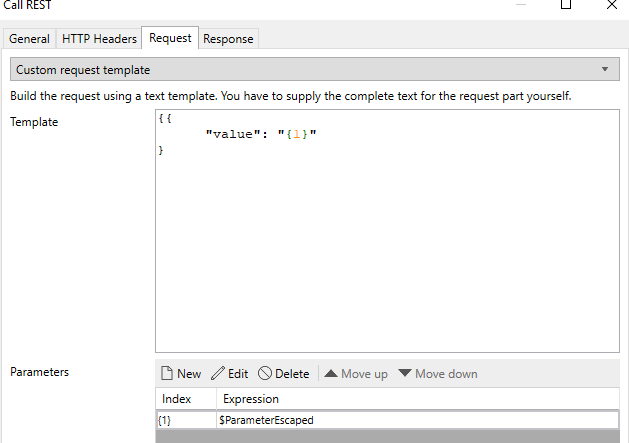
Escaping:
To escape a string for use in JSON a java action can be written and a java JSON library can be used. For example using Google GSON use this code snippet where InputParameter is a string parameter from the Mendix java action:
if (InputParameter==null) return JsonNull.INSTANCE.toString();
JsonPrimitive jp = new JsonPrimitive(InputParameter); // this does the escaping!
String escaped = jp.toString(); // do not use getAsString as it unescapes.
return escaped.substring(1, escaped.length()-1); // since toString places 2 double quotes.