Introduced in version 1.12 (12 August 2020)
A hash algorithm is used to encrypt sensitive information by converting text of the hashed string type to a hash value. Both hash algorithms BCrypt and SSHA256 are secure enough to protect passwords and alike. Mendix recommends to use BCrypt, because it is resistant to brute-force search attacks. However, due to this safeguard, the performance, whilst using BCrypt, might slow down. If you are using a high concurrency of hashing operations, you might consider switching to SSHA256.
See for more information the Mendix documentation.
Non-compliant examples:
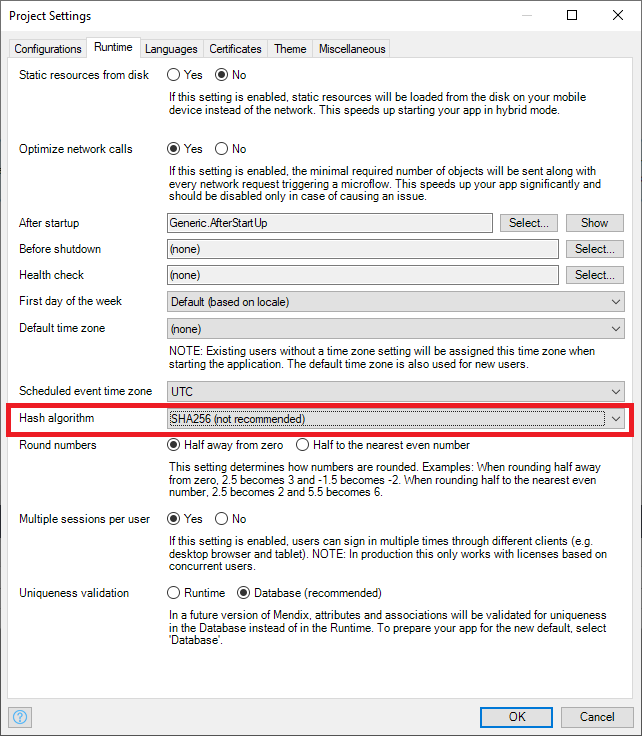
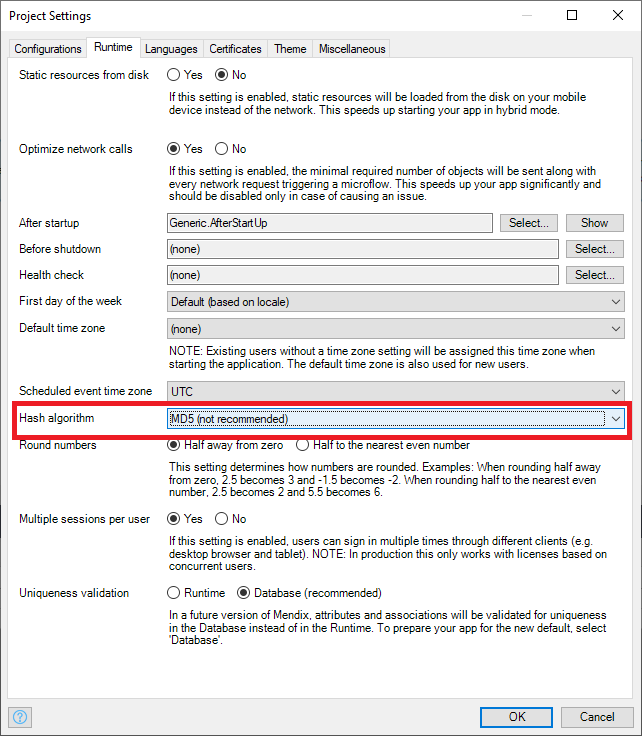
Compliant examples:
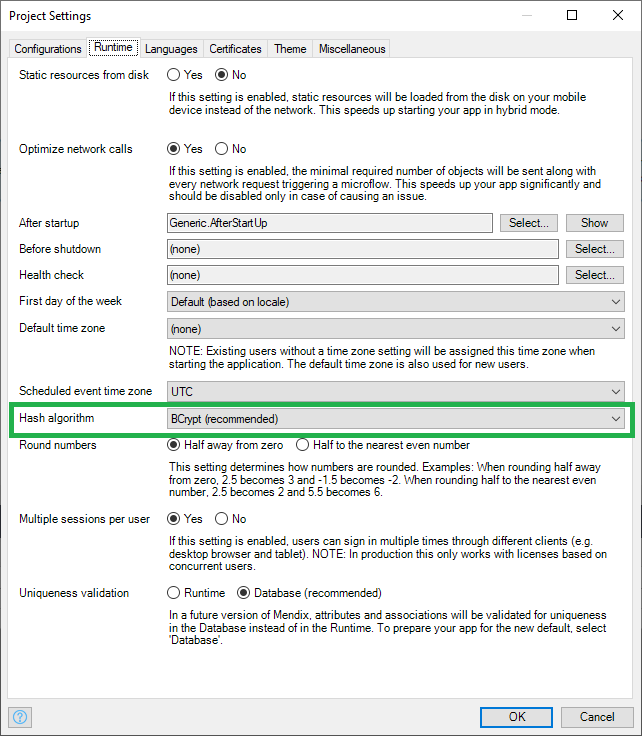
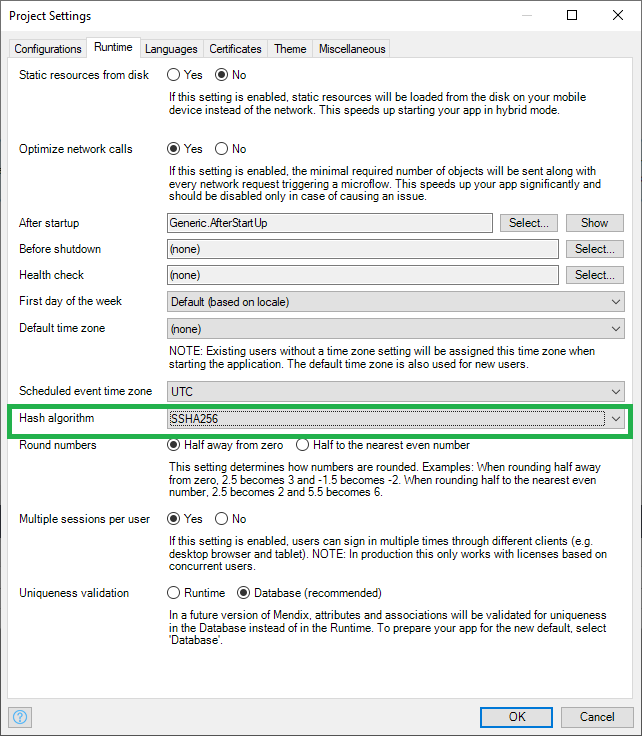
Configure the hash algorithm in Project Runtime Settings and select BCrypt or SSHA256.