Most jar files are created and maintained by third parties and are used as a library of various methods and calls. Over time many vulnerabilities are discovered and fixed in these libraries. If a Java action uses the jar during runtime, such a security vulnerability could cause serious harm to the security of your Mendix application. Good to know that not all vulnerabilities are exploitable. The library’s issues might be in a part that is not executable from your application because it is not exposed through a Java Action or the Java action is not used in your app.
The Java Libraries feature reviews the jar files against the NIST database for security vulnerabilities to give you insight into your Jar files’ security risks.
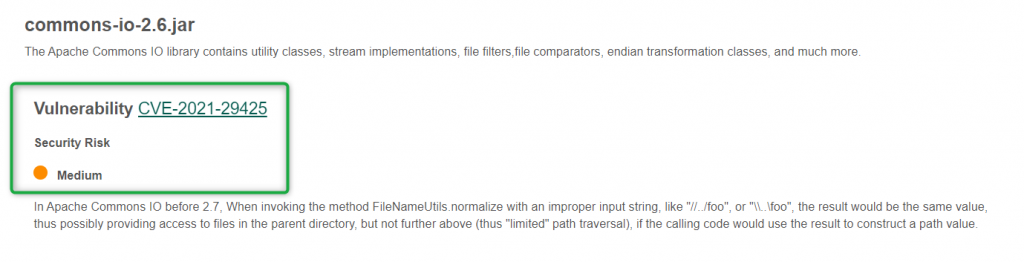
With the Java Libraries feature, we enable Mendix developers to remove potential security risks and improve the overall security of their Mendix application.
How to solve it?
Fixing security vulnerabilities is quite tricky, depending on how the jar is used within the project. However, the following ways could resolve the problem:
- Remove all unused jar files.
- Remove duplicate versions of the jar files.
- Update all modules from the App Store.
- Manual update the dependency to a newer version of decencies and manual fix the Java code.
As with the class loader issue, it is difficult to determine what is unused or a duplication. Updating app store content might not solve the problem. And manually updating the dependency might break the Java action using that specific jar file.
The pain
The pain here is that scanning your jar files for security vulnerabilities isn’t straightforward and that most developers are unaware of these complications. If developers know how to scan the jar files for vulnerabilities, they encounter the same pain as with the classloader issue when solving them. Also, because it might be unclear what jar files are used, the safest approach for every security vulnerability is to fix them because you don’t know how it will impact the application.
Related ACR Rule
– Use user libraries without security vulnerabilities